Incorporating DevSecOps practices can bring more security, compliance, and systems development discipline to organizations looking to move faster in code quality while still considering risk and vulnerability aspects.
So much so that 96% of respondents to a global survey said their organization would benefit from automating security and compliance processes, a fundamental tenet of DevSecOps.
Now, what are the DevSecOps best practices you should be looking for? This is what we will try to answer throughout this article.
What is DevSecOps?
DevSecOps adoption is on the rise: GitLab's annual survey showed that in 2021 more than 36% of respondents said they had already adopted this framework, compared to just 27% in 2020.
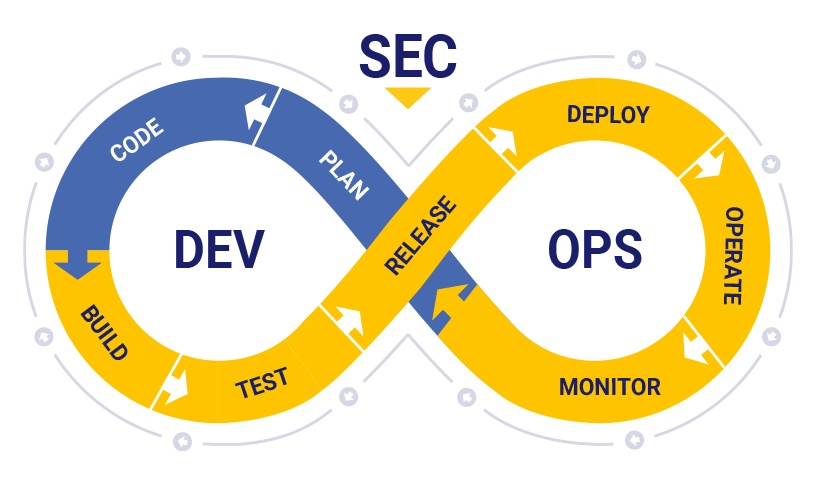
Remember: DevSecOps is a collaboration framework that expands the impact of DevOps by adding security practices to the software development and delivery process. It resolves the tension between DevOps teams that want to release applications quickly and security teams.
By practicing DevSecOps, teams can deliver new software and services at agile speed without compromising application security.
What are DevSecOps best practices?
Having done this brief review of the concept, let's now go to the DevSecOps practices that will make all the difference in your company.
Secure the application development process
The first step in securing the DevOps pipeline is ensuring that the application development process is secure. This means ensuring that only authorized developers have access to code repositories. And that all code changes are reviewed and approved by a qualified reviewer before being merged into the main branch.
It also helps to have trusted developers do the job right and observe cybersecurity best practices throughout.
Protect the production environment
The production environment is where the application will be deployed and used by customers. As such, it is important to ensure that it is as secure as possible.
One way to do this is to segment it into separate layers, each with its own level of access and security controls. That way, even if one layer is compromised, the others will remain protected.
Implement least privilege principles
In general, it is best to follow the principle of least privilege when it comes to granting access to DevOps resources. This means giving users only the permissions they need to do their work and nothing more.
The reason it is so important to follow this is that employees constitute the biggest threat to cybersecurity. This is not always for nefarious reasons, but often because they lack the necessary knowledge or understanding.
Use role-based access control
Role-based access control is a type of access control that can be used to restrict access to DevOps resources based on user roles. For example, you can create a 'developer' role that has access to your code repositories and a 'tester' role that has access to your test environment. By using RBAC, you can help limit the damage that can be caused by an insider threat.
Encrypt confidential data
Any data that could be used to identify or harm an individual must be encrypted, both at rest and in transit. This includes data such as social security and credit card numbers and health information.
One way to encrypt data is to use very good privacy encryption (PGP). PGP uses a combination of public-key and symmetric-key cryptography to protect your data.
Use two-factor authentication
Two-factor authentication is an additional layer of security that can be used to secure access to DevOps resources. With it, a user is required to provide two proofs to verify their identity. The first part is something they know, like a password, and the second part is something they have, like a cell phone.
Implementing this practice helps prevent unauthorized access to resources and systems, even if a user's password is compromised.
Use secret management tools
A secret is any sensitive information that must be kept private, such as a password or API key. Secret management is the process of securely storing and managing secrets.
There are several secret management tools available. They facilitate centralized management of secrets and provide access control and auditing capabilities.
Use a web application firewall
A web application firewall (WAF) is a type of firewall that can be used to protect web applications from attack. WAFs work by inspecting incoming traffic and blocking requests that contain malicious payloads.
Conduct regular security audits
Regular security audits are an important part of DevOps security. They can help you identify weaknesses in your system and ensure your security controls are effective.
There are several different types of security audits, such as penetration testing and code reviews.
Use intrusion detection and prevention systems
Intrusion detection and prevention systems are designed to detect and block malicious activity. They can be used to protect physical and virtual resources.
There are several different intrusion detection and prevention systems available, both open-source and commercial. Some examples of IDPs include Snort, Suricata, and Bro. They are usually deployed as part of a security information and event management system.
Design a disaster recovery plan
A disaster recovery plan is a document that outlines the steps that must be taken in the event of a disaster, breach, or another security incident. It should contain information such as key personnel contact details and procedures for systems restoration.
This type of plan helps to minimize the impact of a disaster and ensure that the organization can recover in a timely manner.
Conduct regular penetration tests
Penetration testing (or pen testing) is a type of security testing that simulates an attack on your system. Its purpose is to identify vulnerabilities that could be exploited by an attacker.
Penetration tests can be performed internally or externally. External penetration tests are often performed by third-party security companies. In-house penetration tests can be achieved by your own team or using a specialized tool.
Wildcard is a NoCode platform that provides a solution to help organizations, and developers, even those without DevOps experience or coding knowledge, to successfully implement and manage versioned infrastructure using NoCode CI/CD pipelines. It enables collaboration, auditing, and automation. You can use Wildcard to build, deploy, and manage applications without writing a single line of code. Start for free by singing using Github or GitLab.

Comments (1)