security
(185)
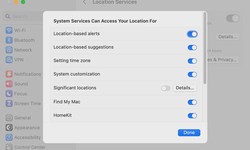
MacOS 13.5: Location privacy broken
The latest Ventura update not only plugs security holes: Apple has also included a gross bug in the system settings. Users of the latest macOS update complain about a security-related problem in connection with the privacy settings. Since the instal...
Kelly · 28 July 2023 · 100Secure Hard Drive Disposal: Protecting Your Data and the Environment
As technology continues to advance, the need for secure and responsible disposal of hard drives has become increasingly important. Proper disposal of hard drives is essential to protect sensitive data and comply with environmental regulations....
SPW Enterprise · 21 June 2023 · 44Gigabyte Motherboards have a firmware backdoor
Researchers from Eclypsium have discovered anomalous behavior on systems with motherboards from the Taiwanese company Gigabyte Technology. The UEFI firmware used in these motherboards, without informing the user during system boot, performed substitution and execution of an executable file for the Windows platform. Subsequently, the executed file w...
Kelly · 01 June 2023 · 64Android becomes a tracker network with a warning about secret trackers
Google will surpass Apple at once when it comes to the reach of Bluetooth trackers. More than 1 billion Android phones help with finding lost items. Google is revamping its "Find my Device" service. By this summer, not only lost Android phones and ta...
Kelly · 11 May 2023 · 137Linux Kernel Vulnerabilities Grant Local Attackers Root Privileges
Two components of the Linux kernel contain security vulnerabilities that grant local attackers root shell access. A first exploit has been made public. Two components of the Linux kernel are affected by security vulnerabilities that allow local attac...
Den W. · 10 May 2023 · 144 · 1Warning about new malware: Attackers can access entire Windows systems
Security experts are warning about malware that allows attackers to gain remote access to Windows PCs. We show you how to protect yourself. The security experts from "Bleeping Computer" are warning Windows users about a new malware called "Lobshot."...
Den W. · 04 May 2023 · 8610 ways to protect yourself from smishing
Mobile phones have revolutionalised how we communicate with each other. We can talk to nearly anyone worldwide, simply by reaching into our pockets. The trouble is that having a phone on you at all times is not only beneficial to you but also to crim...
Alex · 1 year ago · 117Your Main Guide to Vulnerability Assessment and Its Many Types
Vulnerability assessments are used to define, detect, categorize, and prioritize defects and vulnerabilities in applications, devices, and networks that might expose organizations' products, services, code, and applications to attack. Security flaws allow malicious actors to exploit an organization's apps and systems. Comprehensive vulnerability a...
Alex · 30 March 2023 · 44Top 5 Android Hacking Tools for Penetration Testers
Mobile devices are convenient for our lives and can also be used to commit fraud. According to the latest statistics, 70% of online scams occur through mobile platforms. Staggering. But how to avoid them in the first place? Well, android penetration testing is one of the answers. In the realm of ethical hacking, hacking is used to improve system...
Alex · 27 February 2023 · 93Customer Data Security: How to Keep Your Data Secure
It is well established that customer data is one of the most valuable assets that a business can have. At the same time, it is also an asset with one of the highest liabilities. With the increasing importance of digital customer data and the focus on...
Alex · 17 February 2023 · 94Can Reverse DNS Boost Security Significantly?
Reverse DNS isn't a term that many people know. If you have ever wanted to know what it is and how its implementation can help boost your security, then keep on reading! We'll cover the purpose of Reverse DNS, how it works, and the value it brings. So, hop on board and let us help you understand how you can use it to boost. History of Reverse DNS...
Alex · 08 February 2023 · 50How to Change Netflix Region to Access Geo-Blocked Content?
It goes without saying that US Netflix offers the greatest and most varied selection of material available. Even though you pay a monthly membership, you won't be able to use it if you're in Europe or Asia. The good news is that you no longer have to fly abroad to see your favorite program. Continue reading to learn how to safely change your Netfl...
cornerstone · 01 February 2023 · 67Hackers Target iPhones with New Malicious Software
Smartphones like the iPhone produced by Apple are only sometimes safe in locked conditions. If a device has an app called Signal, there's a possibility of the phone getting hacked in the near future. Forbes reports that that's how the forensic team...
Alex · 19 January 2023 · 121Why Automation is Now Essential in Securely Managing Your Cloud’s Attack Surfaces
As more and more businesses shift to the cloud, automation is becoming an essential component of modern security posture management. This is because the dynamic nature of cloud-based operations makes traditional security methods insufficient for miti...
Alex · 06 January 2023 · 96Christmas update for Windows: Microsoft fixes 6 critical vulnerabilities
Microsoft traditionally ends the last Patch Tuesday of the year with fewer patches for Windows, Office & Co. This is also the case this year, although the number of closed security holes has rarely been so high. In addition, however, there are always...
Jacob Enderson · 14 December 2022 · 106How to Achieve Improved Online Security in Internet Banking?
How to Keep Your Internet Banking Safe When online banking initially became available, we know that many of us were afraid to use it because of legitimate security concerns. However, most of us finally agreed that it was quite safe. After that, inter...
Alex · 07 December 2022 · 95