In the relentless pursuit of rapid software delivery, Continuous Integration and Continuous Deployment (CI/CD) pipelines have become the backbone of modern development. However, the need for speed must not eclipse the importance of security. Building secure CI/CD pipelines isn't just a technical practice—it's a strategic imperative that fortifies the entire software lifecycle.
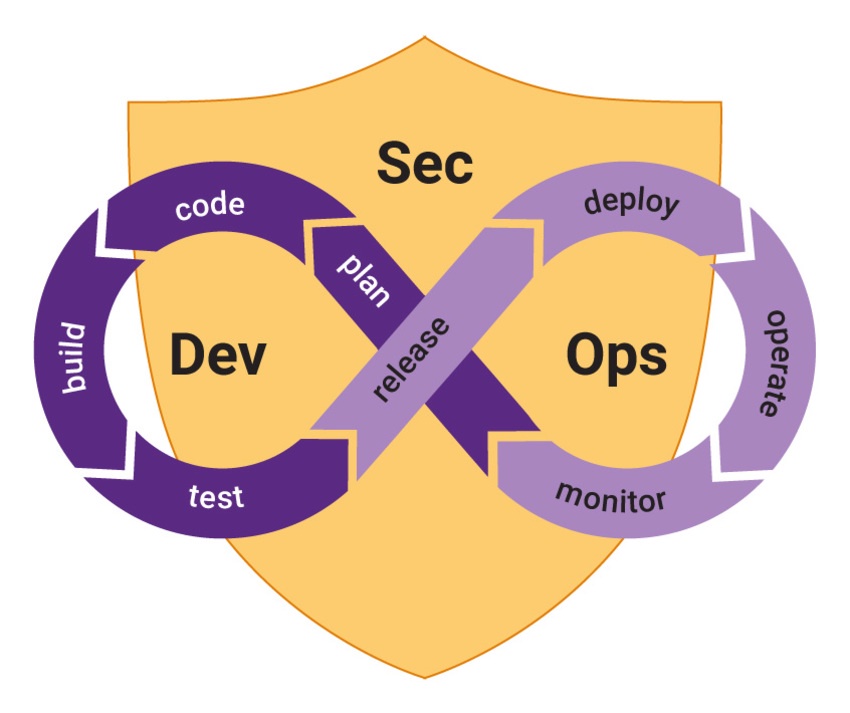
At the heart of secure CI/CD pipelines lies the principle of integrating security checks seamlessly into every stage of development. This requires a holistic approach that transcends traditional silos and empowers developers, operations, and security teams to collaborate in unison. The ultimate goal: to identify and mitigate vulnerabilities at the earliest stages, preventing security issues from escalating downstream.
Stage 1: Planning for Security
The journey towards fortified CI/CD pipelines begins with meticulous planning. Security requirements must be mapped out in alignment with project goals. This stage sets the tone for the entire process, defining the scope of security testing, the selection of relevant tools, and the creation of a comprehensive security checklist.
Stage 2: Source Code Management (SCM)
The foundation of secure pipelines is secure source code. Implement version control, access controls, and code review processes. Automation can enhance these processes, automatically scanning for secrets and vulnerabilities in code repositories.
Stage 3: Automated Code Analysis
Integrate static code analysis into the pipeline. These automated tools analyze code for vulnerabilities, coding standards violations, and potential exploits. Code analysis must be fine-tuned to strike a balance between thoroughness and efficiency.
Stage 4: Dynamic Application Security Testing (DAST)
Incorporate dynamic testing into the pipeline to emulate real-world attacks. DAST tools scan running applications to uncover security vulnerabilities that might not be evident in the code itself. This helps in identifying runtime weaknesses and configuration errors.
Stage 5: Dependency Scanning
Third-party dependencies can be Achilles' heel. Regularly scan dependencies for known vulnerabilities and update them promptly. Automation can streamline this process, alerting teams about potential risks in real time.
Stage 6: Security in Configuration Management
Configuration management is a fertile ground for security lapses. Implement security practices for environment configurations, secrets management, and infrastructure as code (IaC). Secure configuration practices prevent unintentional exposures.
Stage 7: Continuous Monitoring
Security isn't a one-time endeavor—it's continuous. Implement monitoring tools that assess pipelines for security breaches and anomalies. Real-time alerts and automated responses ensure that any deviations are addressed promptly.
Stage 8: Incident Response and Remediation
Preparation for security incidents is just as crucial as prevention. Develop a comprehensive incident response plan that outlines roles, responsibilities, and procedures in the event of a breach. Incorporate automated rollback mechanisms to quickly revert to a secure state.
Stage 9: Employee Training and Awareness
Human error is a persistent challenge. Regularly educate developers and teams about security best practices, emphasizing the importance of their role in maintaining the pipeline's security posture.
In conclusion, building secure CI/CD pipelines is a multidimensional endeavor that marries agility with assurance. Successful integration of security requires a harmonious fusion of technological integration, cultural transformation, and strategic alignment. It's not just about securing code; it's about safeguarding an entire ecosystem against potential threats. In the era of rapid digital transformation, secure CI/CD pipelines are the lighthouses guiding organizations through the treacherous waters of the modern software landscape.

No comments yet