In an era of rapid technological advancement, intelligent security systems have emerged as the vanguard of home protection. These systems go beyond traditional security measures, incorporating cutting-edge technologies that revolutionise how we safeguard our homes. In this article, we will uncover the technologies that power smart security systems. While exploring advancements like artificial intelligence, facial recognition, and cloud computing, we will also delve into lesser-known innovations such as the Jeweller radio protocol from Ajax Systems. So, let's discover the secrets behind these unique features.
The Power of Smart Security Systems
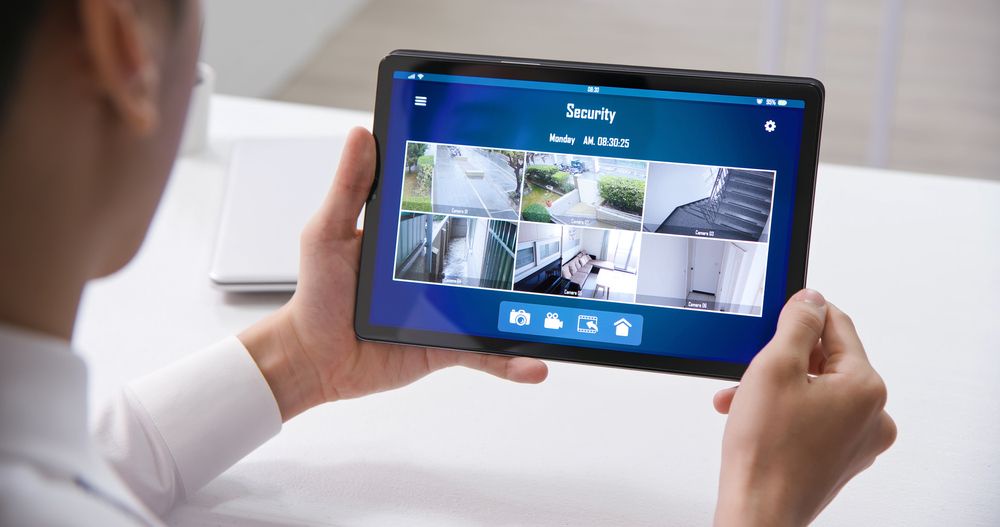
Smart security systems have gained immense popularity due to their ability to provide comprehensive protection and advanced features. They go beyond simple burglar alarms, integrating intelligent technologies with real-time monitoring, personalised security, and remote control capabilities. These systems keep intruders at bay and empower homeowners with peace of mind and a heightened sense of control over their living spaces.
Exploring Cutting-Edge Technologies
A. Artificial Intelligence (AI) and Machine Learning: AI algorithms form the backbone of intelligent security systems. By continuously learning from vast datasets, these systems become adept at recognising patterns and distinguishing between normal and suspicious activities. AI-powered analytics enable smart security systems to identify potential threats accurately, reducing false alarms and providing swift, targeted responses when necessary.
B. Facial Recognition Technology: Facial recognition has evolved by leaps and bounds, finding its place in smart security systems. By analysing unique facial features, these systems can accurately identify authorised individuals and differentiate them from potential intruders. Facial recognition technology enhances security by adding a layer of authentication, making it harder for unauthorised individuals to access protected areas.
C. Cloud Computing: The integration of cloud computing in smart security systems has transformed how we store and access data. With cloud storage, all video footage and system information can be securely stored off-site, reducing the risk of data loss. Cloud-based systems offer the convenience of accessing security footage remotely, allowing homeowners to monitor their properties in real time from anyplace.
D. Advanced Video Analytics: The combination of AI and video analytics has revolutionised the capabilities of smart security systems. These systems can now analyse video feeds in real-time, automatically detecting and tracking suspicious activities or unusual behaviour. With advanced algorithms, security systems can generate instant alerts, enabling homeowners or security personnel to take prompt action.
E. Jeweller Radio Protocol from Ajax Systems: Amidst the cutting-edge technologies driving smart security systems, the Jeweller radio protocol from Ajax Systems deserves special mention. Developed by Ajax Systems, this innovative communication protocol provides secure and reliable wireless connectivity for smart security devices. It ensures robust and uninterrupted communication between sensors, cameras, and the central control panel, creating a robust and responsive security ecosystem.
The Jeweller radio protocol, a proprietary wireless communication technology created primarily for security systems, is the platform on which Ajax motion sensors alarm run. These sensors use the advanced capabilities of Jeweller to enable dependable and effective signal transmission between the sensors and the Ajax security hub. Ajax motion sensors can communicate over a far distance with Jeweller, utilising little power and offering high degrees of signal encryption, increasing the system's overall security. Ajax devices can be seamlessly integrated using the Jeweller protocol, allowing for extensive and customisable security solutions.
The Synergy of Technologies in Smart Security Systems
The true power of smart security systems lies in their ability to integrate multiple technologies seamlessly. The convergence of AI, facial recognition, cloud computing, and advanced video analytics creates a holistic security ecosystem that works in harmony to protect homes. These technologies work hand in hand, sharing data and insights to provide comprehensive security coverage, real-time monitoring, and intelligent responses.
Conclusion
Technologies powering intelligent security systems have transformed how we protect our homes. From the remarkable advancements in AI and facial recognition to the game-changing potential of cloud computing and video analytics, these technologies have unlocked a new era of security. While exploring the remarkable progress in the field, it is crucial to acknowledge innovations like the Jeweller radio protocol from Ajax Systems that contribute to the seamless functioning of these systems. Intelligent security systems will evolve as technology advances, providing homeowners unparalleled safety, control, and peace of mind in an increasingly interconnected world. So, embrace the future, and unlock the potential of smart security systems to safeguard what matters most.

Comments (1)