cybersecurity
(288)
The U.S. Was Hacked for MONTHS, Here’s What We Know So Far
In December 2020, a cybersecurity firm detected a cyberattack on an unprecedented scale. Malicious software had been operating undetected for months, possibly affecting as many as 18,000 organizations — including most U.S. federal government un...
Alex · 03 February 2021 · 84Why Should Cybersecurity Be Your Priority in 2022?
Cyber security incidents are something out of a bad dream, and you wouldn’t want to face this nightmare anytime soon. But unfortunately, these incidents are increasing in sophistication and frequency. Hackers and cybercriminals constantly targe...
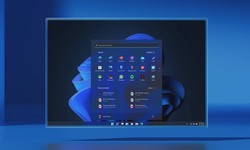
Alex · 30 November 2022 · 86Inside the Mega Glitch: Unlocking Hidden Windows Functions with a Secret Microsoft Tool
This probably wasn't planned this way: During a so-called bug bash for Windows 11, Microsoft employees accidentally shared a link to the StagingTool, a program that is used internally at Microsoft to activate hidden features in Windows 11. Sometimes...
Kelly · 03 August 2023 · 849 Cybersecurity Practices For Staying Safe Against Phishing Attacks
Nowadays, cybercriminals are advancing their efforts in penetrating any company or entity's systems. While you might think your business is exempt from cyber-attacks, think again. The dangers of phishing attacks include severe loss of finances, cruci...
Alex · 19 August 2022 · 80How Much Does an Ethical Hacker Earn in the United States
Hackers have made their mark in cyberspace, with their reputation as the bad guys who use unethical methods to cause harm. However, you can't label all hackers together because some use their skills and expertise for good. These individuals are refer...
Alex · 05 June 2022 · 73Your IT Department: 5 Major Importance and its Role in your Business
There are many reasons why you may need IT support. Perhaps you're experiencing technical difficulties with your computer or other devices, or maybe you simply want to learn more about how to use certain software programs. No matter the reason, it's...
Alex · 03 August 2022 · 69Faster Fixes: Ubuntu's Plan to Reduce Linux Kernel Package Vulnerabilities
Kleber Souza, an engineer at Canonical who maintains Linux kernel packages for Ubuntu, has announced a new kernel update cycle. The new cycle, which is codenamed "4/2", involves generating additional SU kernel package updates (Security Update) that i...
Jacob Enderson · 03 August 2023 · 705 Ways AI Influences Cybersecurity Practices
Cybersecurity is an ever-growing problem as the world becomes increasingly digital. And as our technology becomes more sophisticated, so do cyber attacks. AI technology is continually advancing and has become part of many people’s daily lives....
Alex · 14 August 2023 · 70So you want to be a Security Engineer?
Data is exposed, leaked, stolen and traded every day on the internet. Data breaches are now so common, they no longer become headlines, but mere side notes. Yet companies are spending more and more and more on information security every year, which i...
Alex · 05 November 2020 · 66Learn About the 3 Most Common Scams Made Online - They Will Blow Your Mind!
When the internet first came out, one of the most prevalent pieces of advice was to avoid handing out personal information and talking to strangers. Apps like Uber now bring strangers to our doorsteps so we may take a ride in their automobile. We've...
Talha_Khan · 2 years ago · 68Security threats every software developer should be aware of
Working as a security developer comes with many perks. Flexible working opportunities, a high-demand market, a promising salary, and a bright future ahead of you are just some advantages of the job. However, many people don't know how...
Alex · 15 November 2022 · 67Gigabyte Motherboards have a firmware backdoor
Researchers from Eclypsium have discovered anomalous behavior on systems with motherboards from the Taiwanese company Gigabyte Technology. The UEFI firmware used in these motherboards, without informing the user during system boot, performed substitution and execution of an executable file for the Windows platform. Subsequently, the executed file w...
Kelly · 01 June 2023 · 64Critical Security Vulnerability in Google Chrome
Google has released an update for the Chrome web browser during the night, which addresses at least one critical security vulnerability. This vulnerability allows attackers to smuggle in and execute malicious code. In total, the update includes fixes...
Alex · 1 year ago · 565 Free Online Network Security Courses You Should Follow in 2023
There are numerous online courses for network security, most of which are paid courses, but there are also some open source or government funded free quality courses open to the public. For novices, computer students, administrators and even some jun...
Dayton C. Wilton · 22 December 2022 · 80Web Security Best Practices for Safeguarding Your Website from Cyber Threats
In today's digital landscape, where websites serve as the storefronts and communication hubs for businesses, ensuring robust web security is paramount. Cyber threats are constantly evolving, making it imperative for website owners to implement effect...
Steve Martin · 11 months ago · 49Security updates: Attackers can compromise Aruba switches
Certain switch models from Aruba are vulnerable. The developers have closed a security hole. Network admins should update their Aruba switches to the latest version for security reasons. If this is not done, attackers can compromise the operating sys...
Kelly · 03 August 2023 · 49