security
(204)
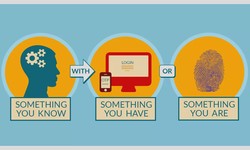
Why You Should Turn On Two Factor Authentication
In 1981, the President of the United States, Ronald Reagan, was shot by a gunman in Washington DC. It wasn’t fatal, but it was close. Reagan was rushed to hospital and in the chaos, the Biscuit went missing. The Biscuit was the nickname given...
Alex · 03 August 2020 · 133How to use the chkrootkit command. Linux Tips
In this Linux tip, we’re going to look at the chkrootkit command. It’s a command that will examine your system for rootkits -- generally malicious software that enables unauthorized access to a system. To install chkrootkit on Ubuntu/Deb...
Jacob Enderson · 02 September 2020 · 4.6KChristmas update for Windows: Microsoft fixes 6 critical vulnerabilities
Microsoft traditionally ends the last Patch Tuesday of the year with fewer patches for Windows, Office & Co. This is also the case this year, although the number of closed security holes has rarely been so high. In addition, however, there are always...
Jacob Enderson · 14 December 2022 · 106How to Change Netflix Region to Access Geo-Blocked Content?
It goes without saying that US Netflix offers the greatest and most varied selection of material available. Even though you pay a monthly membership, you won't be able to use it if you're in Europe or Asia. The good news is that you no longer have to fly abroad to see your favorite program. Continue reading to learn how to safely change your Netfl...
cornerstone · 01 February 2023 · 67How Much Does an Ethical Hacker Earn in the United States
Hackers have made their mark in cyberspace, with their reputation as the bad guys who use unethical methods to cause harm. However, you can't label all hackers together because some use their skills and expertise for good. These individuals are refer...
Alex · 05 June 2022 · 73Secure Hard Drive Disposal: Protecting Your Data and the Environment
As technology continues to advance, the need for secure and responsible disposal of hard drives has become increasingly important. Proper disposal of hard drives is essential to protect sensitive data and comply with environmental regulations....
SPW Enterprise · 21 June 2023 · 44Best Security Approaches for WordPress: Guaranteeing Website Safeguarding
In the fast-paced digital landscape, website security is of paramount importance for businesses and individuals alike. For WordPress websites, being one of the most popular content management systems, robust security measures are essential to protect...
Lucija Petrić · 02 October 2023 · 58Android becomes a tracker network with a warning about secret trackers
Google will surpass Apple at once when it comes to the reach of Bluetooth trackers. More than 1 billion Android phones help with finding lost items. Google is revamping its "Find my Device" service. By this summer, not only lost Android phones and ta...
Kelly · 11 months ago · 137Top 5 Android Hacking Tools for Penetration Testers
Mobile devices are convenient for our lives and can also be used to commit fraud. According to the latest statistics, 70% of online scams occur through mobile platforms. Staggering. But how to avoid them in the first place? Well, android penetration testing is one of the answers. In the realm of ethical hacking, hacking is used to improve system...
Alex · 27 February 2023 · 93Can Reverse DNS Boost Security Significantly?
Reverse DNS isn't a term that many people know. If you have ever wanted to know what it is and how its implementation can help boost your security, then keep on reading! We'll cover the purpose of Reverse DNS, how it works, and the value it brings. So, hop on board and let us help you understand how you can use it to boost. History of Reverse DNS...
Alex · 08 February 2023 · 50PS4 and PS5: Sony can not fix huge security vulnerability
There is a security issue in the PlayStation 4 and PlayStation 5 that is impossible to fix, according to an expert. It is "fundamentally" impossible to fix. Sony has known about the danger for about a year, but has not reacted yet. Hole in PS4 and P...
Alex · 17 September 2022 · 123How to share files and printers in Windows?
When you connect your laptop to a new Wi-Fi network, it's never enough for Windows to just connect you and be done with it. It always asks you this rather cryptic question about whether you want your PC to be discoverable on the network, with a warni...
Alex · 15 July 2020 · 219Ways To Keep Your Anonymous VPS Secure
Online security and reliable hosting service continue to be one of the most discussed topics nowadays. Gone are the days when hackers dwelled in business owners' mistakes and stole vital information. Everyone is now security conscious and continues t...
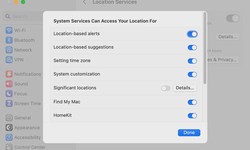
Umer · 23 November 2021 · 130MacOS 13.5: Location privacy broken
The latest Ventura update not only plugs security holes: Apple has also included a gross bug in the system settings. Users of the latest macOS update complain about a security-related problem in connection with the privacy settings. Since the instal...
Kelly · 28 July 2023 · 100GeForce's graphics cards: Nvidia backdoor enables BIOS modifications
With two new flash tools, the BIOS versions of current GeForce graphics cards can be overwritten - even in the RTX 4000 models. Two hobbyists have managed to do what Nvidia has been trying to prevent for years: They have designed tools that allow mod...
Kelly · 21 August 2023 · 5310 ways to protect yourself from smishing
Mobile phones have revolutionalised how we communicate with each other. We can talk to nearly anyone worldwide, simply by reaching into our pockets. The trouble is that having a phone on you at all times is not only beneficial to you but also to crim...
Alex · 20 April 2023 · 117