security
(187)
Faster Fixes: Ubuntu's Plan to Reduce Linux Kernel Package Vulnerabilities
Kleber Souza, an engineer at Canonical who maintains Linux kernel packages for Ubuntu, has announced a new kernel update cycle. The new cycle, which is codenamed "4/2", involves generating additional SU kernel package updates (Security Update) that i...
Jacob Enderson · 03 August 2023 · 70The Evolution of Online Security: Pass Keys vs Passwords
In the ever-evolving landscape of online security, passwords have long been the primary means of authentication. However, even with the assistance of password managers, they come with their fair share of issues. From being hard to remember to the ris...
Jacob Enderson · 01 February · 117Inside the Mega Glitch: Unlocking Hidden Windows Functions with a Secret Microsoft Tool
This probably wasn't planned this way: During a so-called bug bash for Windows 11, Microsoft employees accidentally shared a link to the StagingTool, a program that is used internally at Microsoft to activate hidden features in Windows 11. Sometimes...
Kelly · 03 August 2023 · 84Are You Being Watched? Understanding the Risks of Indoor Smart Cameras
Millions of people across the globe have embraced the convenience of indoor smart cameras in their homes. These devices offer the ability to monitor our surroundings remotely, providing peace of mind and security. However, as we enjoy the benefits of...
Kelly · 09 October 2023 · 7322 Steps to Protect WordPress: Anti-Hacker Security
We have made a compilation of recommendations to protect your WordPress as much as possible. Being the most used content manager in the world, it is quite common for you to receive attacks from hackers, brute force, and robots. If you have all the op...
Alex · 18 July 2022 · 163 · 1Security updates: Attackers can compromise Aruba switches
Certain switch models from Aruba are vulnerable. The developers have closed a security hole. Network admins should update their Aruba switches to the latest version for security reasons. If this is not done, attackers can compromise the operating sys...
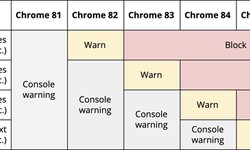
Kelly · 03 August 2023 · 49Chrome will start blocking file uploads via HTTP
Google has published a plan to add new mechanisms in Chrome to protect against unsafe file downloads. In Chrome 86, which is scheduled to be released on October 26th, all types of files will be uploaded via links from pages opened via HTTPS, only whe...
Den W. · 08 February 2020 · 983 · 1Linux Kernel Vulnerabilities Grant Local Attackers Root Privileges
Two components of the Linux kernel contain security vulnerabilities that grant local attackers root shell access. A first exploit has been made public. Two components of the Linux kernel are affected by security vulnerabilities that allow local attac...
Den W. · 10 May 2023 · 144 · 1Customer Data Security: How to Keep Your Data Secure
It is well established that customer data is one of the most valuable assets that a business can have. At the same time, it is also an asset with one of the highest liabilities. With the increasing importance of digital customer data and the focus on...
Alex · 17 February 2023 · 94Hackers Target iPhones with New Malicious Software
Smartphones like the iPhone produced by Apple are only sometimes safe in locked conditions. If a device has an app called Signal, there's a possibility of the phone getting hacked in the near future. Forbes reports that that's how the forensic team...
Alex · 19 January 2023 · 121The Benefits of Guest Networks for Your Wi-Fi Party
So you're hosting a party, and your guests can't be without their precious TikTok for more than five minutes. But before the fun begins, you find yourself fiddling with your router settings, exploring an intriguing option called "enable guest network...
Jacob Enderson · 16 September 2023 · 51Troubleshooting cPanel Issues: Common Problems and Solutions
In the dynamic realm of web hosting, cPanel stands tall as a cornerstone of efficient website management. It’s the dashboard that empowers site owners with the tools to control their digital domains effortlessly. As crucial as it is,...
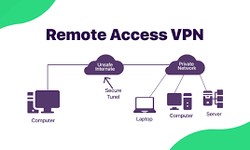
Pooja Naik · 18 December 2023 · 394 Common VPN Types and How To Use Them
There are four common types of Virtual Private Networks (VPN): site-to-site VPNs, personal VPNs, mobile VPNs, and remote access VPNs. But first, why should you Consider a VPN? Since the advent of Virtual Private Networks, it has proven crucial for...
Ahegao Hoodie · 04 June 2022 · 111Why Does Intel Keep Having Security Problems?
In the never ending CPU wars between AMD and Intel, a lot of enthusiasts understandably focus on which of the latest offerings from team red or team blue will give them the best bang for the buck for gaming, streaming and content creation. In other w...
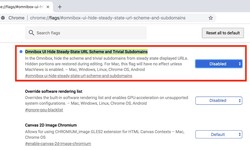
Alex · 30 June 2020 · 56Chrome is going to hide parts of URLs
Web browsing has changed a lot over the years. There's no more Home button, we browse with tabs instead of opening a new window every time, and a GeoCities page, with lots and lots of animated GIFs is no longer the pinnacle of cool. But one thing tha...
Alex · 08 July 2020 · 71Are Google Chrome extensions safe?
One of the most useful things about modern web browsers is their support for extensions, whether it's automatically finding coupon codes. Cleaning up your experience on social media, auto-magically filling in passwords or blocking ads and cutting int...
Alex · 24 July 2020 · 64