security
(187)
cPanel Hosting Security: Best Practices for 2023
cPanel hosting is a popular web hosting solution that provides users with a graphical interface for managing their websites and accounts. While cPanel is a powerful and versatile tool, it is important to secure your cPanel hosting account to pro...
Pooja Naik · 17 January · 222 Steps to Protect WordPress: Anti-Hacker Security
We have made a compilation of recommendations to protect your WordPress as much as possible. Being the most used content manager in the world, it is quite common for you to receive attacks from hackers, brute force, and robots. If you have all the op...
Alex · 18 July 2022 · 163 · 1Troubleshooting cPanel Issues: Common Problems and Solutions
In the dynamic realm of web hosting, cPanel stands tall as a cornerstone of efficient website management. It’s the dashboard that empowers site owners with the tools to control their digital domains effortlessly. As crucial as it is,...
Pooja Naik · 18 December 2023 · 39How To Fix Your Connection Is Not Private Error (100% Legit Methods)
You surely came across the “Connection Is Not Private” error whenever you’re trying to visit a website. We know what brought you here. 95% of the time, people close the tab whenever they see this type of message. BUT we are GLAD th...
Priya Rai · 24 June 2021 · 8389 Cybersecurity Practices For Staying Safe Against Phishing Attacks
Nowadays, cybercriminals are advancing their efforts in penetrating any company or entity's systems. While you might think your business is exempt from cyber-attacks, think again. The dangers of phishing attacks include severe loss of finances, cruci...
Alex · 19 August 2022 · 80Secure Hard Drive Disposal: Protecting Your Data and the Environment
As technology continues to advance, the need for secure and responsible disposal of hard drives has become increasingly important. Proper disposal of hard drives is essential to protect sensitive data and comply with environmental regulations....
SPW Enterprise · 21 June 2023 · 44Why You Should Turn On Two Factor Authentication
In 1981, the President of the United States, Ronald Reagan, was shot by a gunman in Washington DC. It wasn’t fatal, but it was close. Reagan was rushed to hospital and in the chaos, the Biscuit went missing. The Biscuit was the nickname given...
Alex · 03 August 2020 · 133Website Security: The Importance of Backup & Recovery
Introduction Website security is crucial in today’s digital landscape. With threats like hacking, malware, hardware failures, and natural disasters, implementing a robust backup and recovery strategy becomes essential. Explore the role of back...
Pooja Naik · 29 November 2023 · 3How Much Does an Ethical Hacker Earn in the United States
Hackers have made their mark in cyberspace, with their reputation as the bad guys who use unethical methods to cause harm. However, you can't label all hackers together because some use their skills and expertise for good. These individuals are refer...
Alex · 05 June 2022 · 73So you want to be a Security Engineer?
Data is exposed, leaked, stolen and traded every day on the internet. Data breaches are now so common, they no longer become headlines, but mere side notes. Yet companies are spending more and more and more on information security every year, which i...
Alex · 05 November 2020 · 66How to use the chkrootkit command. Linux Tips
In this Linux tip, we’re going to look at the chkrootkit command. It’s a command that will examine your system for rootkits -- generally malicious software that enables unauthorized access to a system. To install chkrootkit on Ubuntu/Deb...
Jacob Enderson · 02 September 2020 · 4.6K10 ways to protect yourself from smishing
Mobile phones have revolutionalised how we communicate with each other. We can talk to nearly anyone worldwide, simply by reaching into our pockets. The trouble is that having a phone on you at all times is not only beneficial to you but also to crim...
Alex · 1 year ago · 117Security threats every software developer should be aware of
Working as a security developer comes with many perks. Flexible working opportunities, a high-demand market, a promising salary, and a bright future ahead of you are just some advantages of the job. However, many people don't know how...
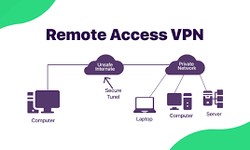
Alex · 15 November 2022 · 674 Common VPN Types and How To Use Them
There are four common types of Virtual Private Networks (VPN): site-to-site VPNs, personal VPNs, mobile VPNs, and remote access VPNs. But first, why should you Consider a VPN? Since the advent of Virtual Private Networks, it has proven crucial for...
Ahegao Hoodie · 04 June 2022 · 111Why Automation is Now Essential in Securely Managing Your Cloud’s Attack Surfaces
As more and more businesses shift to the cloud, automation is becoming an essential component of modern security posture management. This is because the dynamic nature of cloud-based operations makes traditional security methods insufficient for miti...
Alex · 06 January 2023 · 96How to Secure Your Shopify Store from Hackers?
Over the last few years, eCommerce has become an essential part for every business owner because it generates a huge return on investment. In fact, as per the survey, the eCommerce market is expected to reach over $4 trillion, and the figure will gro...
Johnson Lisa · 17 December 2021 · 115