security
(187)
How to use the chkrootkit command. Linux Tips
In this Linux tip, we’re going to look at the chkrootkit command. It’s a command that will examine your system for rootkits -- generally malicious software that enables unauthorized access to a system. To install chkrootkit on Ubuntu/Deb...
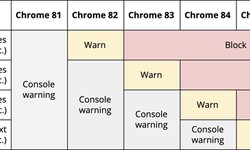
Jacob Enderson · 02 September 2020 · 4.6KChrome will start blocking file uploads via HTTP
Google has published a plan to add new mechanisms in Chrome to protect against unsafe file downloads. In Chrome 86, which is scheduled to be released on October 26th, all types of files will be uploaded via links from pages opened via HTTPS, only whe...
Den W. · 08 February 2020 · 983 · 1How To Fix Your Connection Is Not Private Error (100% Legit Methods)
You surely came across the “Connection Is Not Private” error whenever you’re trying to visit a website. We know what brought you here. 95% of the time, people close the tab whenever they see this type of message. BUT we are GLAD th...
Priya Rai · 24 June 2021 · 838Is Windows Defender Good Enough?
Remember when Norton, McAfee, and Webroot ruled the world, and we were all buying separate antivirus security suites for our computers? These days, many of us have forgotten about these products and instead just opt for the built-in protection offere...
Jacob Enderson · 12 February 2022 · 338How to share files and printers in Windows?
When you connect your laptop to a new Wi-Fi network, it's never enough for Windows to just connect you and be done with it. It always asks you this rather cryptic question about whether you want your PC to be discoverable on the network, with a warni...
Alex · 15 July 2020 · 21922 Steps to Protect WordPress: Anti-Hacker Security
We have made a compilation of recommendations to protect your WordPress as much as possible. Being the most used content manager in the world, it is quite common for you to receive attacks from hackers, brute force, and robots. If you have all the op...
Alex · 18 July 2022 · 163 · 1Linux Kernel Vulnerabilities Grant Local Attackers Root Privileges
Two components of the Linux kernel contain security vulnerabilities that grant local attackers root shell access. A first exploit has been made public. Two components of the Linux kernel are affected by security vulnerabilities that allow local attac...
Den W. · 10 May 2023 · 144 · 1Android becomes a tracker network with a warning about secret trackers
Google will surpass Apple at once when it comes to the reach of Bluetooth trackers. More than 1 billion Android phones help with finding lost items. Google is revamping its "Find my Device" service. By this summer, not only lost Android phones and ta...
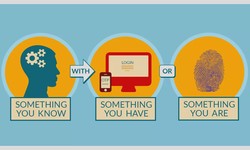
Kelly · 11 May 2023 · 137Why You Should Turn On Two Factor Authentication
In 1981, the President of the United States, Ronald Reagan, was shot by a gunman in Washington DC. It wasn’t fatal, but it was close. Reagan was rushed to hospital and in the chaos, the Biscuit went missing. The Biscuit was the nickname given...
Alex · 03 August 2020 · 133Ways To Keep Your Anonymous VPS Secure
Online security and reliable hosting service continue to be one of the most discussed topics nowadays. Gone are the days when hackers dwelled in business owners' mistakes and stole vital information. Everyone is now security conscious and continues t...
Umer · 23 November 2021 · 130PS4 and PS5: Sony can not fix huge security vulnerability
There is a security issue in the PlayStation 4 and PlayStation 5 that is impossible to fix, according to an expert. It is "fundamentally" impossible to fix. Sony has known about the danger for about a year, but has not reacted yet. Hole in PS4 and P...
Alex · 17 September 2022 · 12310 ways to protect yourself from smishing
Mobile phones have revolutionalised how we communicate with each other. We can talk to nearly anyone worldwide, simply by reaching into our pockets. The trouble is that having a phone on you at all times is not only beneficial to you but also to crim...
Alex · 1 year ago · 117Hackers Target iPhones with New Malicious Software
Smartphones like the iPhone produced by Apple are only sometimes safe in locked conditions. If a device has an app called Signal, there's a possibility of the phone getting hacked in the near future. Forbes reports that that's how the forensic team...
Alex · 19 January 2023 · 121How to Secure Your Shopify Store from Hackers?
Over the last few years, eCommerce has become an essential part for every business owner because it generates a huge return on investment. In fact, as per the survey, the eCommerce market is expected to reach over $4 trillion, and the figure will gro...
Johnson Lisa · 17 December 2021 · 115The Evolution of Online Security: Pass Keys vs Passwords
In the ever-evolving landscape of online security, passwords have long been the primary means of authentication. However, even with the assistance of password managers, they come with their fair share of issues. From being hard to remember to the ris...
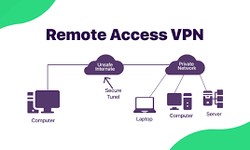
Jacob Enderson · 01 February · 1174 Common VPN Types and How To Use Them
There are four common types of Virtual Private Networks (VPN): site-to-site VPNs, personal VPNs, mobile VPNs, and remote access VPNs. But first, why should you Consider a VPN? Since the advent of Virtual Private Networks, it has proven crucial for...
Ahegao Hoodie · 04 June 2022 · 111