security
(202)
Is Windows Defender Good Enough?
Remember when Norton, McAfee, and Webroot ruled the world, and we were all buying separate antivirus security suites for our computers? These days, many of us have forgotten about these products and instead just opt for the built-in protection offere...
Jacob Enderson · 12 February 2022 · 338Chrome is going to hide parts of URLs
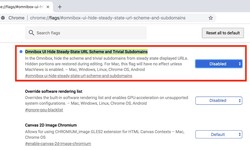
Web browsing has changed a lot over the years. There's no more Home button, we browse with tabs instead of opening a new window every time, and a GeoCities page, with lots and lots of animated GIFs is no longer the pinnacle of cool. But one thing tha...
Alex · 08 July 2020 · 71What Truth About "Cyber Security" SQL Injection Attacks
We live in the golden age of data. Some companies analyze it as a better version of themselves, some companies trade for profit, and no company is free to give up because of its value - for their business and criminals. SQL (Structured Query Languag...
rashidguestpost · 15 October 2022 · 92Why Does Intel Keep Having Security Problems?
In the never ending CPU wars between AMD and Intel, a lot of enthusiasts understandably focus on which of the latest offerings from team red or team blue will give them the best bang for the buck for gaming, streaming and content creation. In other w...
Alex · 30 June 2020 · 56Can Reverse DNS Boost Security Significantly?
Reverse DNS isn't a term that many people know. If you have ever wanted to know what it is and how its implementation can help boost your security, then keep on reading! We'll cover the purpose of Reverse DNS, how it works, and the value it brings. So, hop on board and let us help you understand how you can use it to boost. History of Reverse DNS...
Alex · 08 February 2023 · 50The Benefits of Guest Networks for Your Wi-Fi Party
So you're hosting a party, and your guests can't be without their precious TikTok for more than five minutes. But before the fun begins, you find yourself fiddling with your router settings, exploring an intriguing option called "enable guest network...
Jacob Enderson · 16 September 2023 · 51How to Change Netflix Region to Access Geo-Blocked Content?
It goes without saying that US Netflix offers the greatest and most varied selection of material available. Even though you pay a monthly membership, you won't be able to use it if you're in Europe or Asia. The good news is that you no longer have to fly abroad to see your favorite program. Continue reading to learn how to safely change your Netfl...
cornerstone · 01 February 2023 · 67Android becomes a tracker network with a warning about secret trackers
Google will surpass Apple at once when it comes to the reach of Bluetooth trackers. More than 1 billion Android phones help with finding lost items. Google is revamping its "Find my Device" service. By this summer, not only lost Android phones and ta...
Kelly · 11 months ago · 137The Evolution of Online Security: Pass Keys vs Passwords
In the ever-evolving landscape of online security, passwords have long been the primary means of authentication. However, even with the assistance of password managers, they come with their fair share of issues. From being hard to remember to the ris...
Jacob Enderson · 01 February · 117Understanding HTTPS and Its Role in Internet Security
Most web addresses these days start with https, which implies that your connection to the website is secure in some way. So, what exactly is HTTPS, and how safe is it really keeping you? HTTPS is a protocol that encrypts information sent over the Int...
Kelly · 08 September 2023 · 31Security and Safety in the Online Space: 4 Simple Protection Hacks
Digital innovations and how we interact with them are constantly changing, with our lives quickly becoming more and more interconnected and reliant on digital tools and experiences. Gen Z, the first generation of true digital natives, is now beginni...
Alex · 22 January · 105Linux Kernel Vulnerabilities Grant Local Attackers Root Privileges
Two components of the Linux kernel contain security vulnerabilities that grant local attackers root shell access. A first exploit has been made public. Two components of the Linux kernel are affected by security vulnerabilities that allow local attac...
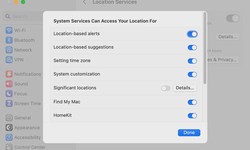
Den W. · 11 months ago · 144 · 1MacOS 13.5: Location privacy broken
The latest Ventura update not only plugs security holes: Apple has also included a gross bug in the system settings. Users of the latest macOS update complain about a security-related problem in connection with the privacy settings. Since the instal...
Kelly · 28 July 2023 · 100Gigabyte Motherboards have a firmware backdoor
Researchers from Eclypsium have discovered anomalous behavior on systems with motherboards from the Taiwanese company Gigabyte Technology. The UEFI firmware used in these motherboards, without informing the user during system boot, performed substitution and execution of an executable file for the Windows platform. Subsequently, the executed file w...
Kelly · 01 June 2023 · 64GeForce's graphics cards: Nvidia backdoor enables BIOS modifications
With two new flash tools, the BIOS versions of current GeForce graphics cards can be overwritten - even in the RTX 4000 models. Two hobbyists have managed to do what Nvidia has been trying to prevent for years: They have designed tools that allow mod...
Kelly · 21 August 2023 · 53Faster Fixes: Ubuntu's Plan to Reduce Linux Kernel Package Vulnerabilities
Kleber Souza, an engineer at Canonical who maintains Linux kernel packages for Ubuntu, has announced a new kernel update cycle. The new cycle, which is codenamed "4/2", involves generating additional SU kernel package updates (Security Update) that i...
Jacob Enderson · 03 August 2023 · 70