security
(187)
So you want to be a Security Engineer?
Data is exposed, leaked, stolen and traded every day on the internet. Data breaches are now so common, they no longer become headlines, but mere side notes. Yet companies are spending more and more and more on information security every year, which i...
Alex · 05 November 2020 · 66How to use the chkrootkit command. Linux Tips
In this Linux tip, we’re going to look at the chkrootkit command. It’s a command that will examine your system for rootkits -- generally malicious software that enables unauthorized access to a system. To install chkrootkit on Ubuntu/Deb...
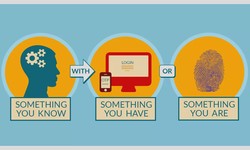
Jacob Enderson · 02 September 2020 · 4.6KWhy You Should Turn On Two Factor Authentication
In 1981, the President of the United States, Ronald Reagan, was shot by a gunman in Washington DC. It wasn’t fatal, but it was close. Reagan was rushed to hospital and in the chaos, the Biscuit went missing. The Biscuit was the nickname given...
Alex · 03 August 2020 · 133Is TikTok a THREAT?
If you're a smartphone enthusiast, you've probably heard about big name Chinese phone manufacturers like ZTE and Huawei being restricted from the US market. So, it may not be terribly surprising that a Chinese app has now come under fire as well. I'm...
Alex · 28 July 2020 · 85 · 1Are Google Chrome extensions safe?
One of the most useful things about modern web browsers is their support for extensions, whether it's automatically finding coupon codes. Cleaning up your experience on social media, auto-magically filling in passwords or blocking ads and cutting int...
Alex · 24 July 2020 · 64How to share files and printers in Windows?
When you connect your laptop to a new Wi-Fi network, it's never enough for Windows to just connect you and be done with it. It always asks you this rather cryptic question about whether you want your PC to be discoverable on the network, with a warni...
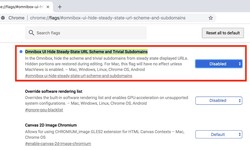
Alex · 15 July 2020 · 219Chrome is going to hide parts of URLs
Web browsing has changed a lot over the years. There's no more Home button, we browse with tabs instead of opening a new window every time, and a GeoCities page, with lots and lots of animated GIFs is no longer the pinnacle of cool. But one thing tha...
Alex · 08 July 2020 · 71Why Does Intel Keep Having Security Problems?
In the never ending CPU wars between AMD and Intel, a lot of enthusiasts understandably focus on which of the latest offerings from team red or team blue will give them the best bang for the buck for gaming, streaming and content creation. In other w...
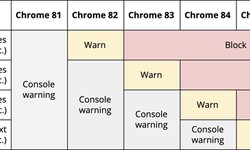
Alex · 30 June 2020 · 56Chrome will start blocking file uploads via HTTP
Google has published a plan to add new mechanisms in Chrome to protect against unsafe file downloads. In Chrome 86, which is scheduled to be released on October 26th, all types of files will be uploaded via links from pages opened via HTTPS, only whe...
Den W. · 08 February 2020 · 983 · 1Creating a Secure Home Environment Residential Security Essentials
In an era of increasing concerns about safety and security, creating a secure home environment is paramount. It encompasses a range of measures designed to protect homes, families, and belongings from various threats. This comprehensive guide explores essential residential security essentials to help you safeguard your home effectively. Understand...
Alpine protection services · 21 hours ago · 1Unified Endpoint Management (UEM)
Today the working environment is not generally restricted to a solitary area or gadget. Employees utilize various gadgets, from cell phones to PCs, to finish their work. Dealing with these gadgets and guaranteeing they are secure and modern is quite...
Vinay Jadhav · 2 days ago · 1Best Security Company in Bristol
In today's fast-paced world, security is paramount for individuals, businesses, and communities alike. With rising concerns about crime, vandalism, and other threats, the demand for reliable security services has never been higher. That's where Titanium Security Services comes in. As the best security company in Bristol, w...
Maxwell Jee · 2 days ago · 3Building a Secure Future Effective Construction Site Security Techniques
Construction sites are dynamic environments with numerous assets, equipment, and personnel. Ensuring the safety and security of these sites is paramount to prevent accidents, theft, vandalism, and unauthorized access. This article delves into effective construction site security techniques that can help build a secure future for construction projec...
Alpine protection services · 2 days ago · 1Unlock Success with SEO Mastery: Discover Atlanta's Top SEO Guru
In the vibrant city of Atlanta, where businesses thrive amidst bustling competition, the key to unlocking success lies in mastering the art of search engine optimization (SEO). Enter SEO Guru Atlanta, the city's top SEO authority, dedicated to helpin...
Evision Atlanta · 5 days ago · 1Vigilance in Action the Role of Construction Site Security Personnel
Construction sites are dynamic environments bustling with activity, equipment, and valuable materials. Among this bustling activity, its personnel play a pivotal role in ensuring the safety and security of assets, personnel, and the site itself. In this inclusive exploration, we delve into the crucial role of site security personnel, examining thei...
Alpine protection services · 5 days ago · 1The Invisible Shield Exploring the Role of Retail Security Systems
In the fast-paced world of retail, protecting assets, ensuring customer safety, and preventing losses are paramount concerns for businesses of all sizes. This security system plays a crucial role in safeguarding stores, merchandise, and employees, providing an invisible shield against various threats. In this inclusive guide, we delve into the role...
Alpine protection services · 6 days ago · 1