security
(187)
Why Should Cybersecurity Be Your Priority in 2022?
Cyber security incidents are something out of a bad dream, and you wouldn’t want to face this nightmare anytime soon. But unfortunately, these incidents are increasing in sophistication and frequency. Hackers and cybercriminals constantly targe...
Alex · 30 November 2022 · 86Security threats every software developer should be aware of
Working as a security developer comes with many perks. Flexible working opportunities, a high-demand market, a promising salary, and a bright future ahead of you are just some advantages of the job. However, many people don't know how...
Alex · 15 November 2022 · 67What Truth About "Cyber Security" SQL Injection Attacks
We live in the golden age of data. Some companies analyze it as a better version of themselves, some companies trade for profit, and no company is free to give up because of its value - for their business and criminals. SQL (Structured Query Languag...
rashidguestpost · 15 October 2022 · 92More performance with Windows 11: You shouldn't listen to these Microsoft tips
More performance with Windows 11: You shouldn't listen to these Microsoft tips Windows 11 users have complained about the poor gaming performance. The company now offers tips to improve the performance. However, it is better to avoid them, because t...
Alex · 11 October 2022 · 96How Did Hacking Become the Next Trend for TryHackMe?
The red team hacker academy is all you need to know to get the best results from hacking. If you are interested to know how to get into cyber security, then it's a lot better to register for the TryHackMe website. It's the only website that gives you...
Alex · 27 September 2022 · 83PS4 and PS5: Sony can not fix huge security vulnerability
There is a security issue in the PlayStation 4 and PlayStation 5 that is impossible to fix, according to an expert. It is "fundamentally" impossible to fix. Sony has known about the danger for about a year, but has not reacted yet. Hole in PS4 and P...
Alex · 17 September 2022 · 1239 Cybersecurity Practices For Staying Safe Against Phishing Attacks
Nowadays, cybercriminals are advancing their efforts in penetrating any company or entity's systems. While you might think your business is exempt from cyber-attacks, think again. The dangers of phishing attacks include severe loss of finances, cruci...
Alex · 19 August 2022 · 80Top 8 Helpful Security Apps for Your Mobile Phone
So, do you need antivirus software on your phone, taking up extra space, slowing you down, and sending you a barrage of annoying notifications? More than 86% of smartphones worldwide run Android, compared to less than 15% running iOS. It's no surpris...
Setsuna Lake · 03 August 2022 · 5222 Steps to Protect WordPress: Anti-Hacker Security
We have made a compilation of recommendations to protect your WordPress as much as possible. Being the most used content manager in the world, it is quite common for you to receive attacks from hackers, brute force, and robots. If you have all the op...
Alex · 18 July 2022 · 163 · 1How Much Does an Ethical Hacker Earn in the United States
Hackers have made their mark in cyberspace, with their reputation as the bad guys who use unethical methods to cause harm. However, you can't label all hackers together because some use their skills and expertise for good. These individuals are refer...
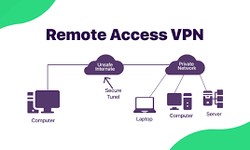
Alex · 05 June 2022 · 734 Common VPN Types and How To Use Them
There are four common types of Virtual Private Networks (VPN): site-to-site VPNs, personal VPNs, mobile VPNs, and remote access VPNs. But first, why should you Consider a VPN? Since the advent of Virtual Private Networks, it has proven crucial for...
Ahegao Hoodie · 04 June 2022 · 111Seecrets on Stability A Gentle Intro on Cryptography
A somewhat prolonged list of content "Retaining Your Guidelines Strategy" will have a look at smart ideas in more element and offer very helpful advice and tips. Certainly, these will continue with the style of making crypto and computer stability re...
Johnthomas · 09 May 2022 · 71Is Windows Defender Good Enough?
Remember when Norton, McAfee, and Webroot ruled the world, and we were all buying separate antivirus security suites for our computers? These days, many of us have forgotten about these products and instead just opt for the built-in protection offere...
Jacob Enderson · 12 February 2022 · 338How to Secure Your Shopify Store from Hackers?
Over the last few years, eCommerce has become an essential part for every business owner because it generates a huge return on investment. In fact, as per the survey, the eCommerce market is expected to reach over $4 trillion, and the figure will gro...
Johnson Lisa · 17 December 2021 · 115Ways To Keep Your Anonymous VPS Secure
Online security and reliable hosting service continue to be one of the most discussed topics nowadays. Gone are the days when hackers dwelled in business owners' mistakes and stole vital information. Everyone is now security conscious and continues t...
Umer · 23 November 2021 · 130How To Fix Your Connection Is Not Private Error (100% Legit Methods)
You surely came across the “Connection Is Not Private” error whenever you’re trying to visit a website. We know what brought you here. 95% of the time, people close the tab whenever they see this type of message. BUT we are GLAD th...
Priya Rai · 24 June 2021 · 838